
|
Generic part of Security Services in CACIB
Security Features
Security, privacy and confidentiality of our customers’ information are of paramount importance to us.
We are committed to protecting the customer against third party fraud by providing a secure online banking environment through the use of proven industrial security standards and practices, such as (and not limited to) firewalls, intrusion detection mechanisms, encryption, security alert processes, dedicated security watch teams, incident management etc.
Please note that Credit Agricole CIB banking services means all services provided by Credit Agricole CIB and that a Client can access (corporate and FI clients)
All information transmitted via our websites are fully encrypted from password, User ID to account / transactions details.
Each of these sites uses an up-to-date SSL Certificate that you can check the following way:
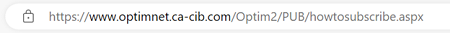
Select "The connection is secure"
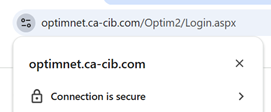
Click on the Padlock to display details,
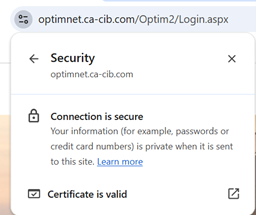
Then click on the Certificate icon to display its characteristics.
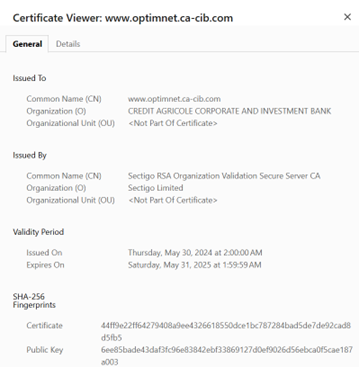
Our certificates always have these common characteristics:
- Organisation name: CREDIT AGRICOLE CORPORATE AND INVESTMENT BANK
- Issued by: Sectigo RSA
Should you be asked to connect to a website displaying a certificate with different properties, it would mean you have been directed to a fake Credit Agricole CIB web site. Please disconnect immediately and report us the address in that case. Please notify by phone or email your local “Credit Agricole CIB Banking Service*” representative or simply send us an e-mail by clicking on “Contact Us” on the web banking home page.
Main security features and procedures that have been adopted are:
- Industry approved encryption
All information transmitted via our applications is secured and encrypted through the use of the industry’s most current and secure encryption technology (check certificates for details)
Verification of the domain name can be viewed by clicking on the ’lock’ icon which will display certification details of the issuing Certificate Authority.
- Digipass / Soft Token Identification
Access to our transactional websites is protected by strong authentication system of user id (Digipass / Soft Token ID) (alphanumeric & case sensitive) and a Digipass / Soft Token personal identification number (PIN). Only by providing the system with the correct combination will the customer be allowed to access to its Web Banking content.
- Authentication means are adapted to the security stakes of the website proposed. Automatic time-out/logout
Transactional web sites will automatically logout a user session should it detect inactivity after a short period of time. This is done to prevent unauthorized usage, should the system be left alone or if the customer has forgotten to logout. This is compliant as well with regulations request (e.g. PSD2).
- Security devices
Credit Agricole CIB internet facing infrastructures embed multiple layers of firewalls, intrusion detection devices, reverse proxies, etc. The architectures are constantly monitored to detect unauthorized intrusions attempts and activities.
- Security Services 24/7
Credit Agricole CIB and the Credit Agricole Group have a permanent security watch in place through a CERT (Computer Emergency Response Team), called the CERT AG (CERT-AG Credit Agricole)
The Credit Agricole Group also has a centralized SOC (Security Operation Center) that dispatches to Credit Agricole Group entities all security alerts that may occur on their perimeter.
Credit Agricole CIB has dedicated additional teams in place to manage incident and alerts, be they Operational ones or Security ones. A central 24/7 follow the sun team is in place to manage this (Computer Security Incident Response Team –CSIRT) and liaise with the IT staff in charge of infrastructures and applications.
Processes are in place to manage incidents, and Credit Agricole CIB has a strong crisis management culture in place in cooperation with the BCP Manager.
Security Measures and Users role
The user plays an important role to fight against online fraud.
He is responsible for safeguarding and keeping secret and confidential his account details and/or his User ID and/or his Digipass-Soft Token and/or Digipass-Soft Token ID and/or PIN (when applicable) and for ensuring that none of them are compromised in any way.
In particular the user should:
- ensure that he does not knowingly or accidentally disclose or allow access to his User ID and/or Digipass-Soft Token ID, and/or PIN (when applicable) including any other authorized “Credit Agricole CIB Banking Service” users of the customer;
- destroy the original printed copy of his User ID and/or his initial PIN and Digipass-Soft Token ID (as applicable) received from the Bank;
- never write down the User ID and/or Digipass-Soft Token ID, and/or PIN on any device for accessing any “Credit Agricole CIB Banking Service ” or on anything usually kept with or near it;
- never write down or record the User ID and/or Digipass-Soft Token ID, and/or PIN (as applicable) without disguising it; and
- change its PIN (if applicable) on a regular basis - eg every 30 days.
Credit Agricole CIB will never contact customers to ask them to validate personal information such as any User ID, PIN and/or Digipass-Soft Token ID and customers should never disclose sensitive information, such as their User ID, PIN or Digipass-Soft Token ID to anyone including to any of our employees or to the police.
If the customer receives such a request, he must immediately notify by phone or email his local “Credit Agricole CIB Banking Service” representative or simply send us an e-mail by clicking on "Contact Us" on its web banking home page.
When choosing a PIN (as applicable), the customer should:
- not create it using easily accessible personal information such as telephone numbers or date of birth, ID numbers or a recognizable part of his name;
- avoid using the same PIN (as applicable) for accessing other services (eg, for accessing other web sites or ATMs or phone banking PINs) or a Password or PIN which has previously been used for other “CACIB Banking Service”;
- choose a PIN (as applicable) of length of 6 digits that may be difficult for someone else to guess, and without repeating any digit more than once.
To guarantee the best level of security, user accounts that have not logged in at all on a “Credit Agricole Banking Service” for a certain period of time may be blocked and/or deleted. Controls
If the computer used by the customer to access “Credit Agricole CIB Banking Service” is likely to be shared with others, users should exercise care in using “Credit Agricole CIB Banking Service”.
Sharing of computers to access “Credit Agricole CIB Banking Service” is not recommended and users should NOT use the “Credit Agricole CIB Banking Service” in public places such as cyber cafes.
Never use a computer or a device which cannot be trusted to connect to “Credit Agricole CIB Banking Services”.
After users have accessed a “Credit Agricole CIB Banking Service”, they should not leave their computer unattended and they must lock their session in case they need to leave temporarily.
Once users have finished using any “Credit Agricole CIB Banking Service”, they should log-off properly and promptly to avoid leaving the computer online whilst they are not using the service.
Physical tokens (Digipass) must be kept in a safe place, which cannot be accessed by parties other than the authorized holder.
Do not select the “browser option” for storing or retaining username and password.
If the computer has internet access via cable modems, broadband connections or similar set-ups, the file and printer sharing should be removed.
Please turn off your computer when it is not in use.
Actions on clients’ side
Clients are strongly advised:
- To install suitable firewall and virus protection software on their computers, to provide protection against hackers who may try to gain access to the user’s files and/or download viruses or keystroke loggers;
- To keep their Operating System up to date with the latest version or security patches;
- To download new browser security patches whenever they are available, and to update to the latest version whenever possible;
- Not to open e-mail attachments or access suspicious websites unless the user knows that they are safe and from a reputable source;
- Delete junk or chain emails;
- Not to install pirated software or software from unknown providers;
- Make regular backup of critical data;
- Consider the use of encryption technology to protect highly sensitive data.
In case the client workstation is a corporate managed device, IT & Security department must be consulted to ensure the above recommendations are in place. Reporting of Actual or Suspected Security Incidents, and
Transaction Irregularities / Disputes
All transactions through the Internet bear inherent risks. To minimize and to protect against such online risks, the security and safety of online banking depends on both the bank’s security systems and measures taken by the clients.
Clients are advised to regularly check their account balances and statements to identify any unusual transactions.
In case of unusual transaction(s) or abnormal information, clients must call/contact the Bank’s appointed local representative for the concerned service used, or simply send us an e-mail by clicking on "Contact Us" on the web banking home page.
A Client should contact Credit Agricole CIB when he suspects that:
- User ID and/or Digipass-Soft Token ID or PIN code of one or several of its users has/have been disclosed to a third party or has/have been lost or stolen or otherwise compromised;
- One or several Digipass has/have been lost or stolen;
- Any unauthorized transactions may have taken place through their accounts;
- There has been some unusual account activity or an unusual last logon time-stamp;
- There are any irregularity and/or dispute in transactions;
- Client information displayed appear erroneous or inadequate;
- If a user leaves the company or move to another position that impacts his access rights.
If the user contacts us via phone, followed by written confirmation with relevant details, support staff will advise him on the immediate course of action to be taken. If necessary, the access to the concerned “Credit Agricole CIB banking service” may be suspended during the investigation period in order to protect the interest of the client. To facilitate our investigations (especially if it relates to disputed / irregular transactions), the customer is requested to provide the following information:
- Description of the error / issue encountered
- Type of transaction
- Date of transaction
- Our transaction reference number
- Account number
- Amount
- Customer name and contact number
Global Security Tips
Numerous suspected Trojan Horse attack cases related to business/corporate Internet banking offered by banks have been detected in the recent years, as well as countless phishing attempts of different kind targeting users or corporates.
In order to help customers detect and prevent such attacks, please see the below security tips for your reference:
- During the Internet banking logon process, the bank will not ask customers to enter any numbers displayed on the web into the security code.
- Customers should continue to take precautionary measures to keep their computers safe to guard against Trojan Horse attacks, including:
- Install personal firewall and anti-virus software in their personal computers and keep them up-to-date.
- Be very cautious about opening attachments in e-mails from unfamiliar sources, and avoid visiting or downloading software from suspicious websites.
- Never access the Internet banking accounts through hyperlinks embedded in emails, Internet search engines, suspicious pop-up windows or any other doubtful channels.
- Customers should connect to a bank website through typing the authentic website address in the address bar of the browser or by bookmarking the genuine website and using that for subsequent access.
- If customers find the website of the bank suspicious, they should not enter any information (including user ID, password and OTP) to the website and should report to the bank immediately.
- If any unusual screens pop up and/or the computer responds unusually slowly, customers are advised to log out from Internet banking and scan the computer with the most updated version of virus protection software.
- Don’t disclose any personal information to any person through any means.
- Review the transaction records regularly and report to the bank immediately if any suspicious transactions in the bank accounts are identified.
- Follow the Internet banking logon instructions and security tips published by the Bank when conducting Internet banking transactions.
Phishing attacksPhishing attacks are the most common way to attack clients and Companies used by hackers. On the Client side- Be vigilant against phishing attempts. Always carefully check if the sender of an email is legitimate, and be aware that a real address may also be spoofed in some cases (ex: when the attacker does not expect a reply to the email but simply wants the target to open a trapped attachment, or have the target follow a hyperlink to a fake site).
- Do not open dubious messages from unknown senders.
- Do not open attachments they may contain.
- Do not activate macro-commands contained in external email attachments by default.
- Ensure Macro commands are deactivated by default and require manual activation to be executed in your Office environment.
- In case you use a corporate device, ensure this setting is in place by asking your Security or IT team.
Do not follow dubious links contained in such emails. Main phishing techniques used by hackers
- Spear phishing
This is a targeted phishing strategy. The fraudster would collect precise and rich data on the internet about the targeted representative of a company (public information and social network to collect personal information, contacts, career path, etc.). Then the fraudster would be in position to send an e-mail appearing well founded with information in the e-mail and sender appearing to be valid. Confident, the targeted company representative would respond positively to the request. Confidential information, such as passwords, customer data or company organization, could thus be recovered and used for malicious purposes.
Ways to prevent these cyber-attacks:- Think and take a few moments before replying (email, phone call, SMS);
- Be vigilant;
- Control your data, especially on social networks;
- Cross-check and verify information;
- If in doubt or if you have shared data, report it quickly.
- Angler phishing and smishing
Through various channels, a real person or a robot will impersonate an organization or individual known to the target, to induce this target to communicate sensitive information.
For example, if the target is attacked on social networks, this is known as angler phishing. Many companies communicate with their users via social networks, whether for promotional or informational purposes. The fraudster can for example pretend to be the official profile of a company to extract information from its victim.
The smisher likes to approach his target by text message. He may even post a company name instead of a phone number or insert themselves into an existing discussion thread.
It is also common for a person to be enticed to call a phone number. The fraudster on the other end of the line is the visher. He often pretends to be a technician ready to help.
Having gained the victim trust, he tricks his targets into divulging information.
- Fake President
The fraudster takes the identity of an important person in the company and, with the pretext of urgency and confidentiality, asks the victim to perform transactions which are fraudulent.
Ways to prevent this scenario:- Be vigilant even if the request comes from a senior official;
- Comply with internal procedures;
- Make counter-checks or counter-calls.
- Quishing
Fraudster would use a QR code through flyers or any type of printed material distributed to its targets.
It can also be sent by e-mail, often beyond security systems because QR codes are generally perceived as images.
After scanning it with their business phone, victims are redirected to a malicious website where they are asked to enter their credentials.
Ways to prevent these cyber-attacks:- Be vigilant: find out where the documents you receive come from;
- Control your connection data;
- Cross-check and verify information;
- If in doubt or if you have shared data, report it quickly to your usual Credit Agricole CIB contact or using the “Contact us” functionality on the web banking homepage.
- Fraud through USB Stick
Imagine you find an unknown USB stick and connect it to your professional smartphone to discover who is the owner and what is the content. Once the stick is connected, viruses will be installed on the victim’s device, which can then spread between different types of devices, such as a computer and a storage device.
Ways to prevent these cyber-attacks:- Be vigilant: never use tools that don’t belong to you;
- If in doubt or if you have shared data, report it quickly.
- Fraud through a wifi network
While travelling you may decide to connect your computer to a public WIFI network. This network can be an alias created by a fraudster. The level of risk would depend if it is a personal or professional laptop and network. In the worst case, all details of the documents may be shared.
Ways to prevent these cyber-attacks:- Work exclusively on your professional network, which may be protected by a VPN;
- Don’t share files or work outside of the professional environment;
- If in doubt or if you have shared data, report it quickly.
- Morphing
By borrowing faces and voices, fraudsters can impersonate anyone in the company. Most often, it impersonates highly influential persons, with the goal of sending false messages and obtaining sensitive information.
Ways to prevent these cyber-attacks:- Think carefully and take a few moments before clicking;
- Be vigilant: check the URL link before clicking;
- Control your connection data, especially on public networks;
- If in doubt or if you have shared data, report it quickly.
- Fraud using Pharming
Via a link, a pop-up window or even a file containing macros such as Word or Excel, the fraudster will install malicious code on the target’s device or network that will act in the background.
Reflexes against these cyber attacks:- Never click on links from pop-ups;
- Check that the online site you are visiting uses HTTPS.
- Rogue Recovery
The goal is to gain access to one of his target’s accounts by using password recovery methods to bypass multi-factor authentication.
Simple reflexes against these cyberattacks exist however:- Be vigilant;
- Never transfer a verification code;
- If in doubt or if you have shared data, report it quickly.
|